In the realm of data-driven business operations, having a clear insight into user activities and system interactions is pivotal for success. Salesforce, a global leader in CRM solutions, provides a powerful tool called the EventLogFile object to empower organizations with comprehensive visibility into their Salesforce environment. In this blog, we will delve into the significance of the EventLogFile object, its applications, and showcase its use through a real-world example.
Understanding the EventLogFile Object:
The EventLogFile object is an essential part of Salesforce's event monitoring framework, allowing organizations to capture a diverse range of events within their Salesforce instance. These events include user logins, data access, changes to records, report executions, and more. By accessing and analyzing data from EventLogFile records, businesses can uncover valuable insights into user behavior, troubleshoot issues, and enhance security.
Applications of the EventLogFile Object:
1. Comprehensive Monitoring:
The EventLogFile object enables organizations to monitor various events occurring in their Salesforce environment, providing a comprehensive overview of user interactions and system activities.
2. Security Analysis:
By analyzing EventLogFile data, organizations can detect patterns indicative of potential security breaches, unauthorized access, or suspicious behavior. This empowers them to proactively address security threats.
3. Operational Insights:
EventLogFile data offers insights into user behaviors, system performance, and application interactions. These insights can be used to optimize processes, enhance user experiences, and troubleshoot issues.
Example Scenario: Identifying Unauthorized Data Access
Consider the following scenario: A sales representative for your organization, just quit to work for a major competitor. You start losing business to this other company all of a sudden. According to your suspicions, the sales representative may have downloaded a private lead information report and shared it with his new company. You wouldn’t usually be able to validate your assumptions. However, using Salesforce Event Monitoring may acquire all of the evidence you need to clear up the situation. Let’s have a look at how this works.
Step 1: Data Collection
The organization configures EventLogFile object tracking to capture data access events. This includes events such as track, troubleshoot, and audit your organization's user activity.
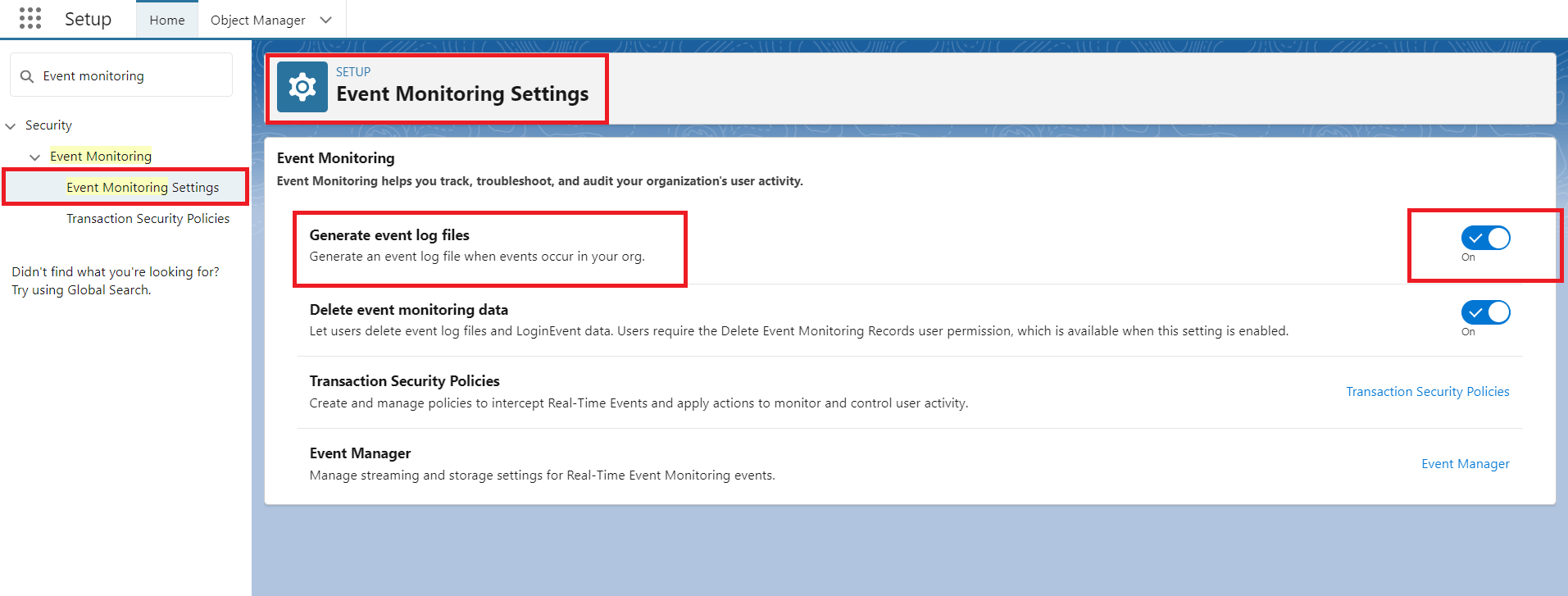
Figure 1: Configure Event monitoring setting in salesforce org.
Step2: Open the EventLogFile.
- pen Developer Console.
- Select File > Open from the File menu. After this, select the Objects from the Entity Types drop-down menu.
- Type EventLogFile in the Filter repository field. Under Entities, choose EventLogFile.
- Click the Open button.
- Click the Query button after selecting the fields for your query.
- To complete the query, click the Execute button.
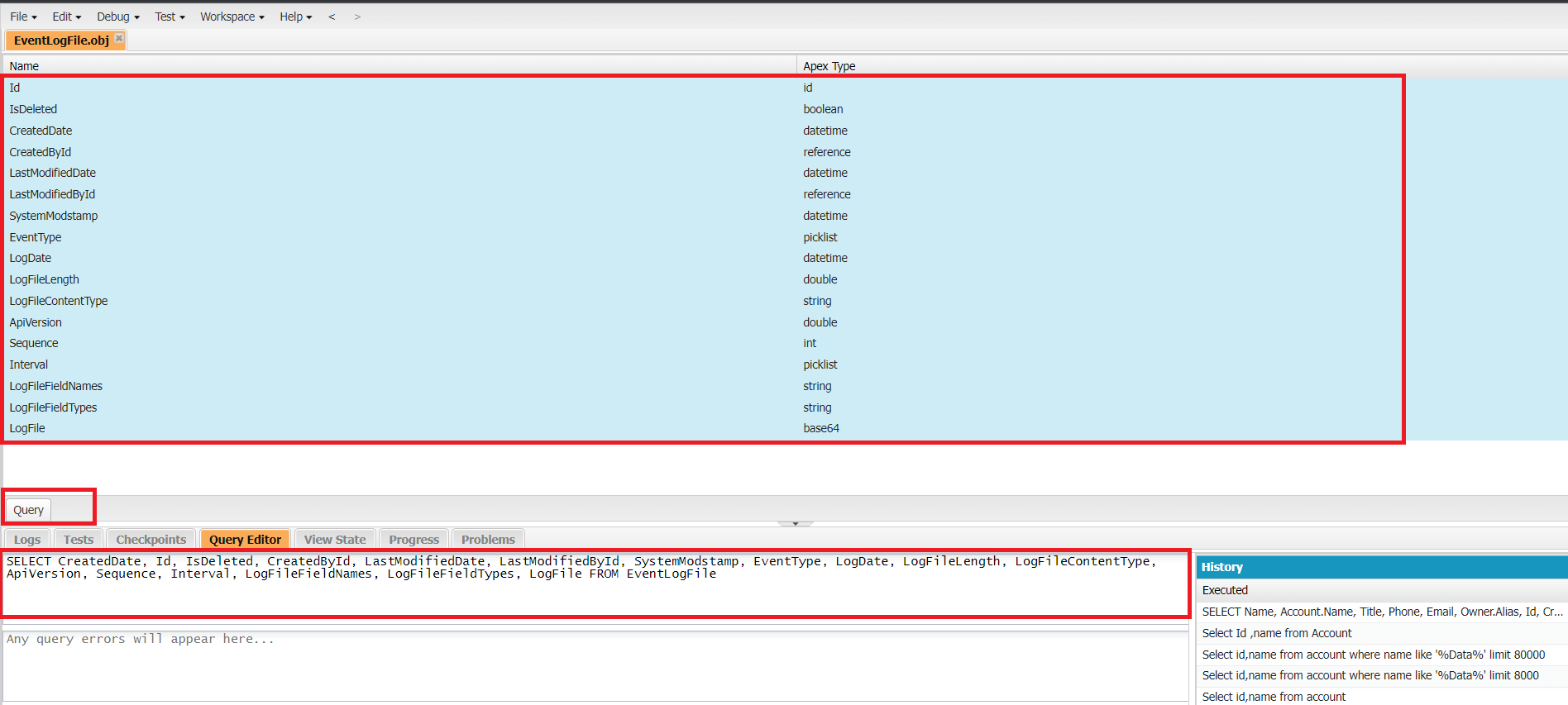
Figure 2:Select the fields and click on ‘Query’ to generate a query to fetch log files.
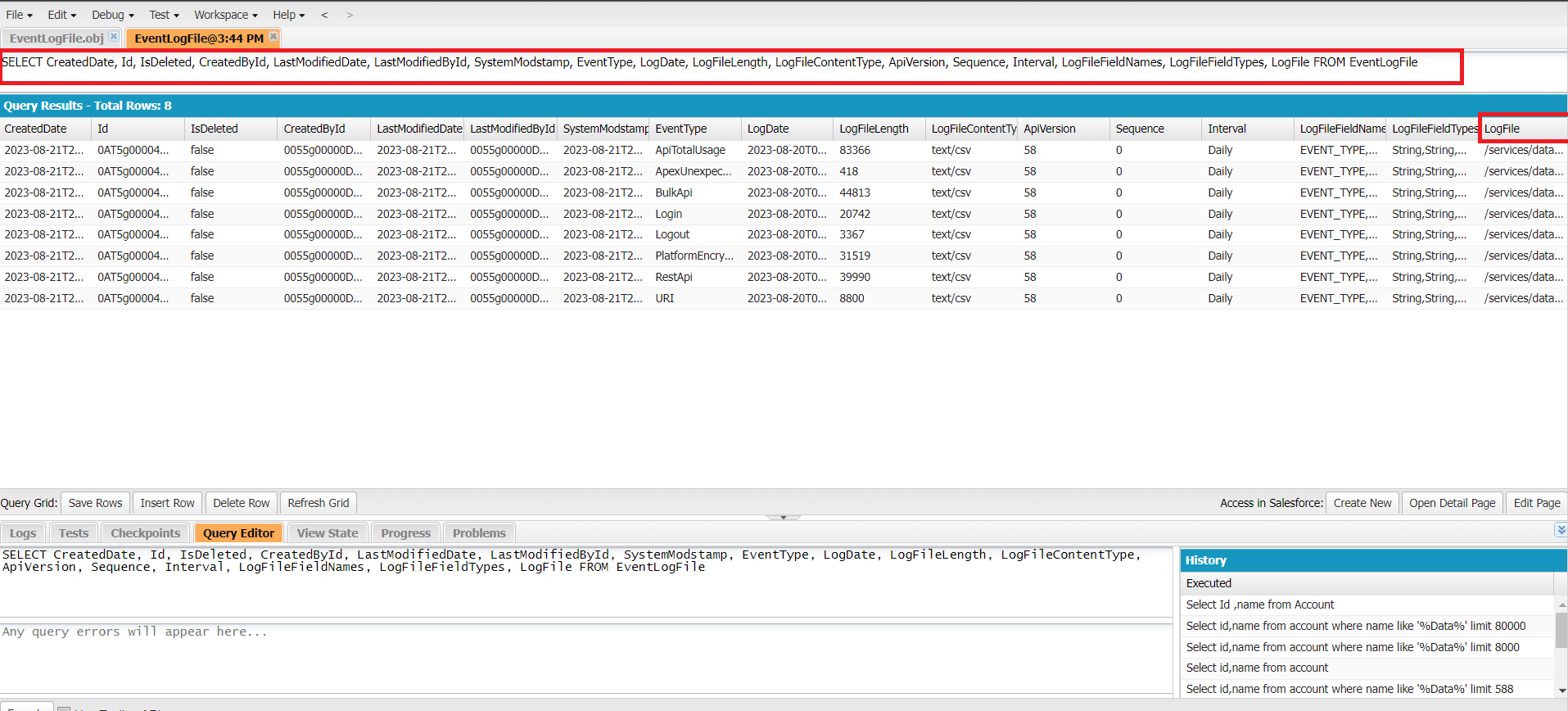
Figure 3: Fetched data from query with selected fields and also fetched log files.
Step3: View the Salesforce Event LogsFile
- Log in to your org.
- Navigate to the ELF Browser application.
- Click Production Login.
- Enter a date range for your search.
- Enter an event type for your search.
- Enter an interval (daily or hourly).
- Click Apply.
- Find Id of LogFile in ELF Browser Application.
- Click the direct download button to download a log to a comma-separated values (.csv) file.
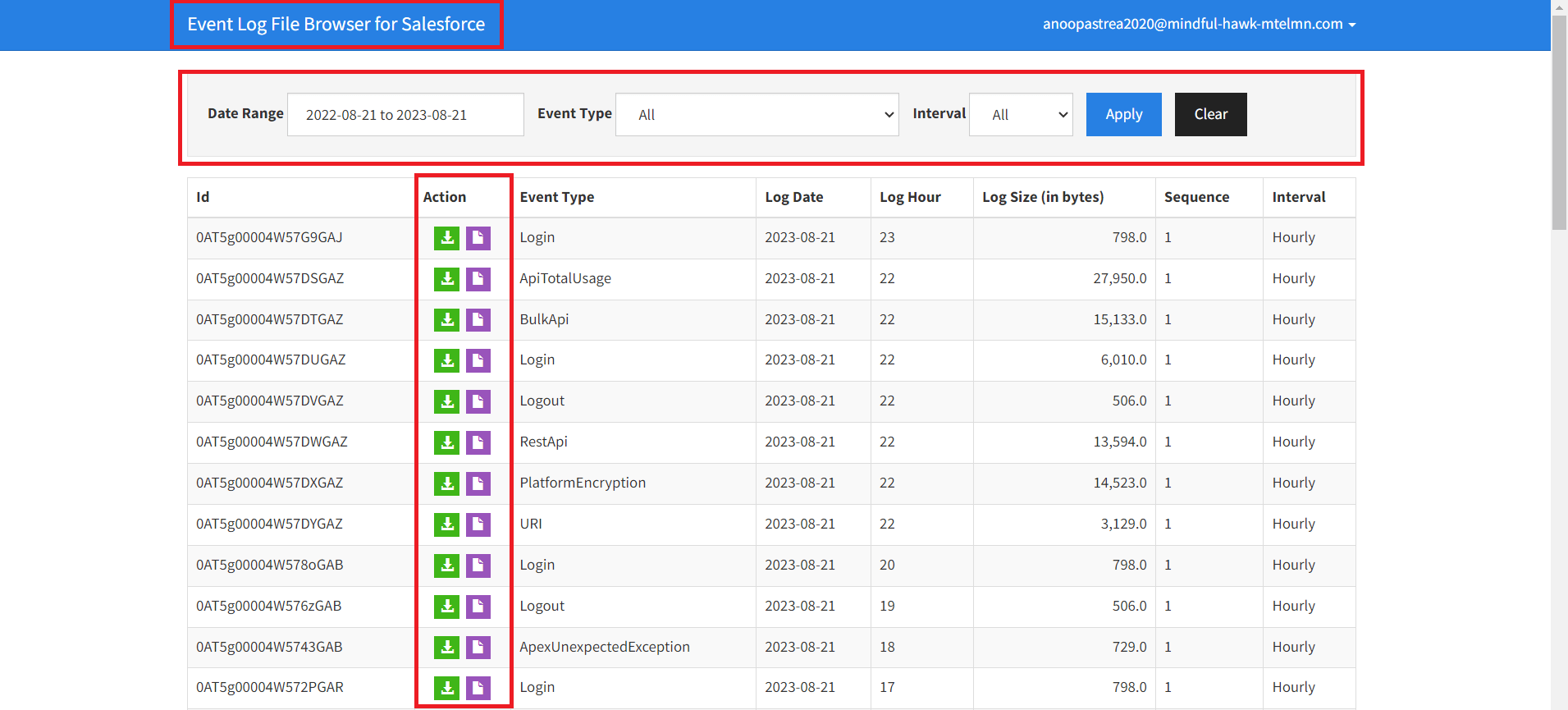
Figure 4: Open ELF Browser Application and Apply filter to get relevant data and click on download button to download file in csv format.
Download the ReportExport log file. Open it in a spreadsheet, and let’s see what we can find.
Figure 5: A .csv file which contains all event data as per filter conditions apply on ELF browser.
Step 4: Analyzing EventLogFile Data
By analyzing the EventLogFile data, the security team identifies suspicious activity into org.
Step 5: Mitigation and Reporting
The Suspicious activity is mitigated, and a report is generated using EventLogFile data to document the incident for regulatory compliance purposes.
Conclusion:
The EventLogFile object in Salesforce stands as a testament to the platform's commitment to data security, insights, and compliance. By providing a granular view of user activities and system interactions, this object empowers businesses to enhance security measures, optimize operations, and make informed decisions. The EventLogFile object is more than just a tool; it's a gateway to understanding the dynamics of your Salesforce environment, ensuring that data remains secure, users stay engaged, and operations run smoothly in an ever-evolving digital landscape.
For any queries please reach out to support@astreait.com.